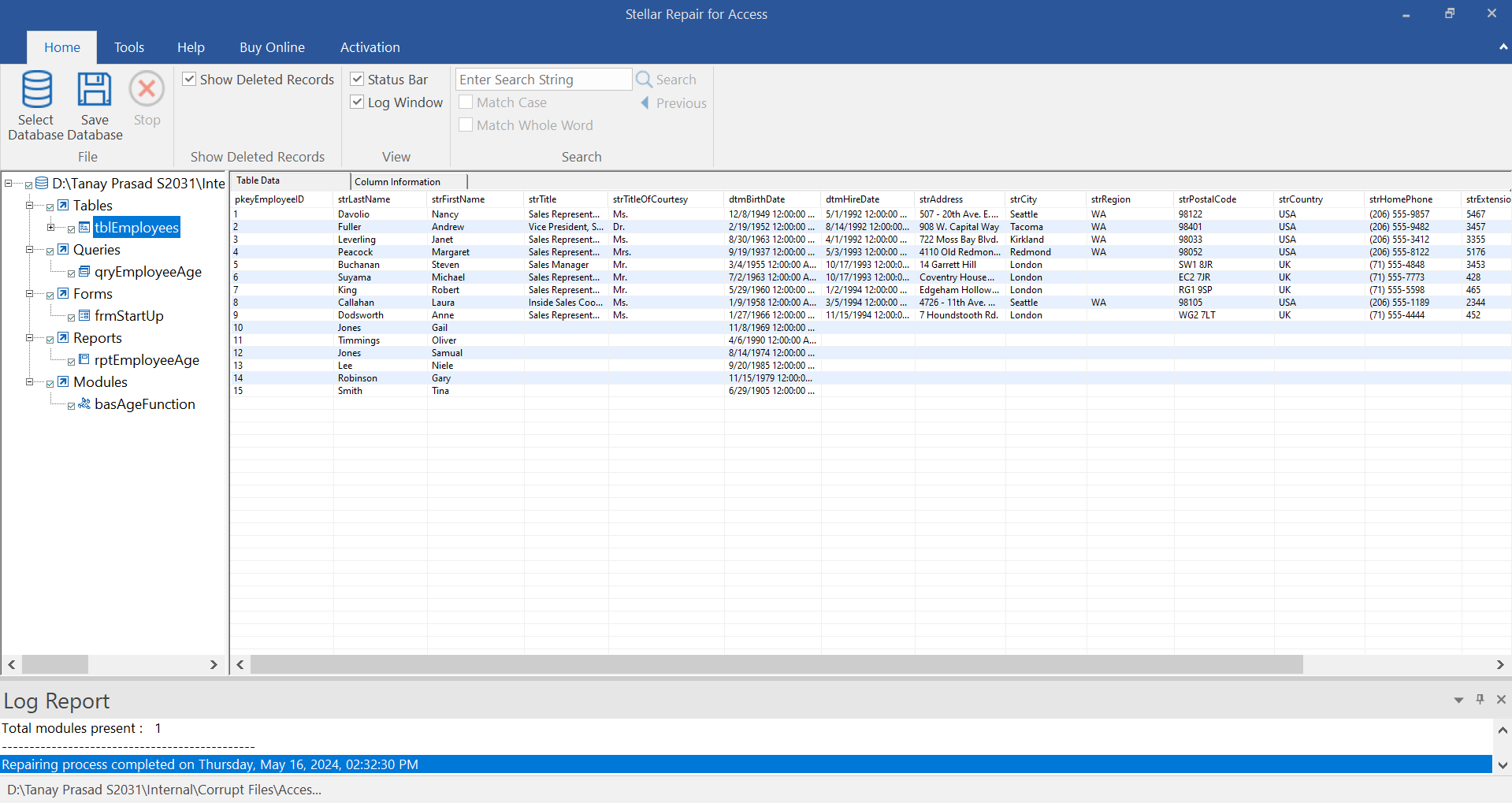
How To Fix Database Open Access Vulnerability . vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. To fix this issue in the products that are listed in “applies to,” install the following security update, as. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. please enter the description for this article.a scan engine found that sentry is effected with database open. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. Do not restricting direct access of databases to the remote systems.
from www.stellarinfo.com
Do not restricting direct access of databases to the remote systems. please enter the description for this article.a scan engine found that sentry is effected with database open. To fix this issue in the products that are listed in “applies to,” install the following security update, as. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. to learn about how to implement vulnerability assessment in azure, see implement vulnerability.
How to Compact & Repair Access Database from Command Line
How To Fix Database Open Access Vulnerability Do not restricting direct access of databases to the remote systems. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. please enter the description for this article.a scan engine found that sentry is effected with database open. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. To fix this issue in the products that are listed in “applies to,” install the following security update, as. Do not restricting direct access of databases to the remote systems. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security.
From www.accessrepairnrecovery.com
7 Troubleshooting Ways To Repair & Recover Corrupt Access database Forms How To Fix Database Open Access Vulnerability please enter the description for this article.a scan engine found that sentry is effected with database open. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. To fix this issue in the products that are listed in “applies to,” install the following security update, as. vulnerability assessment includes actionable steps to resolve security. How To Fix Database Open Access Vulnerability.
From www.bestshareware.net
Vulnerability Repair Tool designed to detect and fix vulnerabilities How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. To fix this issue in the products that are listed in “applies to,” install the following security update, as. to learn about how to. How To Fix Database Open Access Vulnerability.
From www.stellarinfo.com
How to Compact & Repair Access Database from Command Line How To Fix Database Open Access Vulnerability vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. please enter the description for this article.a scan engine found that sentry is effected with database open. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. To fix this issue in the products. How To Fix Database Open Access Vulnerability.
From blog.bitrise.io
5 Tips to Help You Identify and Fix Open Source Vulnerabilities Bitrise Blog How To Fix Database Open Access Vulnerability To fix this issue in the products that are listed in “applies to,” install the following security update, as. please enter the description for this article.a scan engine found that sentry is effected with database open. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. attackers can use sql injection on an. How To Fix Database Open Access Vulnerability.
From nordicapis.com
How To Fix Broken Access Control Nordic APIs How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. To fix this issue in the products that are listed in “applies to,” install the following security update, as. Do not restricting direct access of databases to the remote systems. vulnerability assessment includes actionable steps to resolve security issues. How To Fix Database Open Access Vulnerability.
From www.youtube.com
Broken Access Control Vulnerability Attack 2023 owasptop10 Explanation practical training How To Fix Database Open Access Vulnerability vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. To fix this issue in the products that are listed in. How To Fix Database Open Access Vulnerability.
From www.activestate.com
How to remediate your open source vulnerabilities quicker ActiveState How To Fix Database Open Access Vulnerability vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. Do not restricting direct access of databases to the remote systems. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and.. How To Fix Database Open Access Vulnerability.
From www.stellarinfo.com
How to Compact and Repair Access Database using How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. To fix this issue in the products that are listed in “applies to,” install the following security update, as. please enter the description for this article.a scan engine found that sentry is effected with database open. to learn. How To Fix Database Open Access Vulnerability.
From www.youtube.com
How to Compact and Repair a Database in MS Access Office 365 YouTube How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. Do not restricting direct access of databases to the remote systems. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. To fix this issue in the products that are listed in “applies to,” install the. How To Fix Database Open Access Vulnerability.
From www.thesslstore.com
OpenSSL Issues Update to Fix Formerly ‘Critical’ Vulnerability Nov. 1 Hashed Out by The SSL Store™ How To Fix Database Open Access Vulnerability vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. To fix this issue in the products that are listed in “applies to,” install the following security update, as. please enter the description for. How To Fix Database Open Access Vulnerability.
From www.freeviewer.org
ACCDB Viewer Tool Open Access Database Files 2016, 13, 10, 07, 03 How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. Do not restricting direct access of databases to the remote systems. To fix this issue in the products that are listed in “applies to,” install the. How To Fix Database Open Access Vulnerability.
From customerthink.com
How IPS & IDS Work Together for Threat Remediation CustomerThink How To Fix Database Open Access Vulnerability To fix this issue in the products that are listed in “applies to,” install the following security update, as. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. please enter the description for. How To Fix Database Open Access Vulnerability.
From www.manageengine.com
What is Vulnerability Management? Definition & Process ManageEngine Vulnerability Manager Plus How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. To fix this issue in the products that are listed in. How To Fix Database Open Access Vulnerability.
From developers.redhat.com
Vulnerability analysis with Red Hat CodeReady Dependency Analytics and Snyk Intel Red Hat How To Fix Database Open Access Vulnerability please enter the description for this article.a scan engine found that sentry is effected with database open. To fix this issue in the products that are listed in “applies to,” install the following security update, as. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. Do not restricting direct access of databases to the. How To Fix Database Open Access Vulnerability.
From www.accessrepairnrecovery.com
How to Fix Runtime Error 3167 Record Is Deleted Microsoft Access? How To Fix Database Open Access Vulnerability Do not restricting direct access of databases to the remote systems. please enter the description for this article.a scan engine found that sentry is effected with database open. attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. To fix this issue in the products that are listed in. How To Fix Database Open Access Vulnerability.
From www.stellarinfo.com
How to Compact and Repair Access Database Without Opening How To Fix Database Open Access Vulnerability please enter the description for this article.a scan engine found that sentry is effected with database open. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. To fix this issue in the products that are listed in “applies to,” install the following security update, as. to learn about how to implement vulnerability. How To Fix Database Open Access Vulnerability.
From medium.com
Understanding and Preventing SQL Injection Vulnerabilities in Applications by josue How To Fix Database Open Access Vulnerability to learn about how to implement vulnerability assessment in azure, see implement vulnerability. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. Do not restricting direct access of databases to the remote systems. To fix this issue in the products that are listed in “applies to,” install the following security update, as. . How To Fix Database Open Access Vulnerability.
From www.dnsstuff.com
Top 15 Paid and Free Vulnerability Scanner Tools DNSstuff How To Fix Database Open Access Vulnerability attackers can use sql injection on an application if it has dynamic database queries that use string concatenation and. vulnerability assessment includes actionable steps to resolve security issues and enhance your database security. to learn about how to implement vulnerability assessment in azure, see implement vulnerability. Do not restricting direct access of databases to the remote systems.. How To Fix Database Open Access Vulnerability.